What is phishing?
Phishing is a scheme where hackers get users to share sensitive information, like passwords and social security numbers. It typically involves sending spam email that looks like it's coming from a trusted source, such as a bank (that's the bait), that then links to a fraudulent website impersonating the trusted source (this is the trap).
Understanding what these attacks look like and how they work can help you spot phishing attempts, as well as give you some information about what to do if your website has been compromised to host a phishing trap.
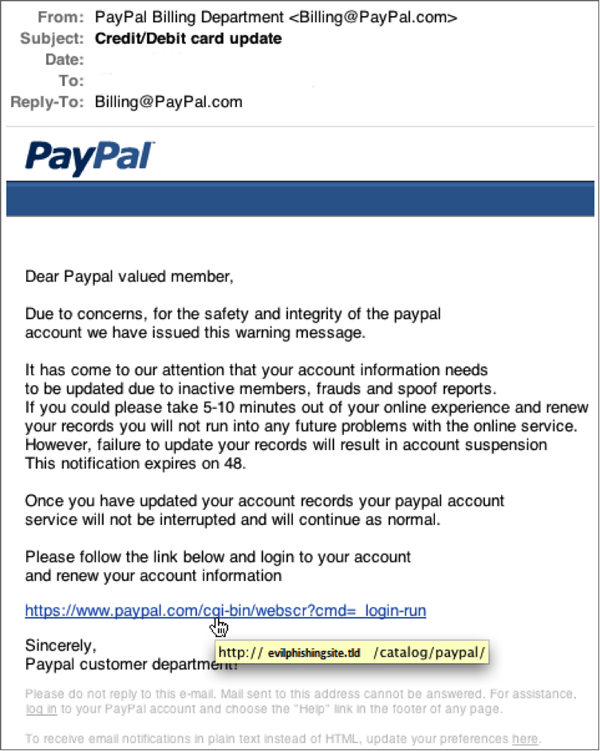
Phishing email (Bait)
Phishing emails impersonate trustworthy organizations to steal user credentials. In the example below, the email employs a common phishing practice, asking users to update their account information. However, when you hover over the link, it doesn't lead to the company's actual website — it leads to a phishing trap site instead.
Phishing website (Trap)
Sometimes the only way to tell that a website is an impersonation is to look at the webpage’s URL. For example, in the image above, the page might look like it’s from PayPal, but the URL shows that it’s not legitimate.
Here's an example of a convincing phishing page:
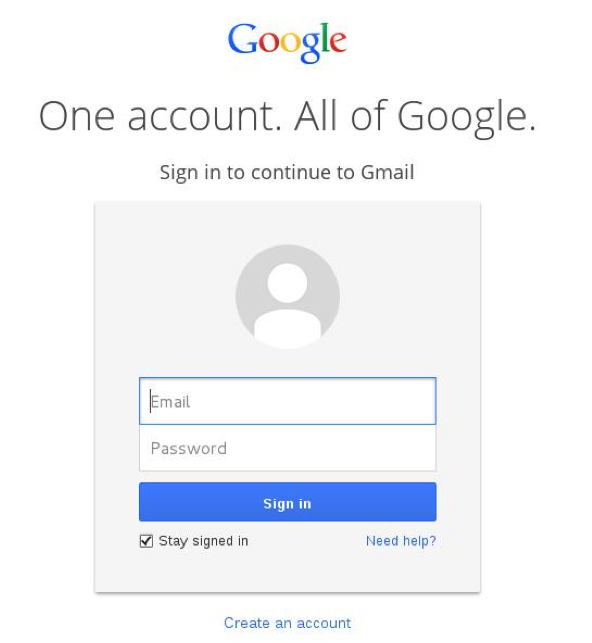
The only way to tell this isn't the actual Google sign-in page is to look at the browser's address bar. In this example, you'd notice the domain name isn't actually google.com.
For example, in http://login.google.com.evilphishingsite.com/index.html, the site you're really on is evilphishingsite.com.
Phishing sites hosted on your account
If your site suffers an FTP compromise, hackers might use your account to host a phishing website. For next steps, see
My website was hacked. What should I do?When you view your files and directories, you can be sure that the directories named after well-known businesses (such as banks or Google) are being used for phishing. For example:
- ./html/HSBC/hsbc.com/
- ./html/Gmail/googledocs/Googledock/
Related step
- You can report phishing here.
More info
Check out the following resources on phishing and how to protect yourself:
- Home page for the Anti-Phishing Working Group (APWG)
- Advice from the Federal Trade Commission: How to Recognize and Avoid Phishing Scams
- Info from PayPal: How to identify fake messages