Business email compromise (BEC) is on the rise, with some research studies suggesting that the practice is growing by as much as 19% a year.
It has never been more important for you to understand what BEC is and how to strengthen your email security.
In this blog, we tackle the most frequently asked questions about business email compromise, also known as a BEC scam.
- What is a business email compromise?
- What’s the difference between BEC and phishing attacks?
- How common is business email compromise?
- What’s the cost of an email business compromise?
- What’s an example of a business email compromise?
- Four signs of a BEC attack
- How can I protect my business against a BEC scam?
- What to do if you fall victim to business email compromise
What is business email compromise?
Business email compromise is a form of social engineering, where criminals use deception to get something they want. The BEC scam tries to trick a member of a business — or their clients or suppliers — into sending money via wire transfer or sharing sensitive information.
BEC is an umbrella term for cyberattacks that can include spear phishing, spoofing, impersonation and fake invoices.

Criminals involved in BEC scams hack into the email accounts of either an employee of the business itself or a supplier, partner or affiliate of the business.
Then, once they have gained access to these email accounts, they send out fake email requests from that account.
If the recipients aren’t on their guard, they could assume this is a legitimate email since it’s coming from a familiar email address.
The content of these fake emails varies but they can include:
- An email threat demanding for payment
- A fake invoice
- A request for the recipient to change the bank account details of a supplier
- Links to harmful websites
- Viruses disguised as innocent-looking attachments
- A legal demand that involves a request for payment or a link to an unsafe site or file
There’s also a particular type of BEC attack that’s known as CEO fraud or a whaling attack.
In these attacks, the criminal gains access to the email account of a CEO or other senior executive.

Once they have access, they impersonate the CEO or senior executive in emails to staff members, asking them to:
- Make urgent payments
- Send funds, sometimes via wire transfer
- Click on malicious links
Again, unless they know what to look for, there’s a good chance they’ll respond. No one ignores an email from the CEO of their company.
Related: 6 email scams to look out for
How do criminals gain access to emails?
There are a number of ways hackers take control of employee's email accounts to carry out monetary or data theft. These include:
Fake password reset emails: hackers send the victim an email that mimics one from their email provider. The email asks them to reset their password for one reason or another. When the recipient changes their password, the hacker steals their login data.
Using details leaked in a data breach: if your password was leaked in a data breach and you use the same password for multiple accounts, a hacker can attempt to use the leaked data to log in to your email account.

Malware: hackers can install malicious software on your device that copies sensitive data like your login details and passwords. Malware can be installed on your device in a number of ways, including when you:
- Open infected attachments
- Visit an unsafe website
Weak passwords: if you use a password like 1234567 or querty or changemeplease, then a hacker can take a pot-luck approach to gain access to your email account.
What’s the difference between BEC and phishing attacks?
While phishing emails are sent out unselectively to thousands of people, BEC scams are more targeted.
They’re more sophisticated, too.
In regular phishing emails, the email address is a dead giveaway that the email is a scam. As the hacker does not have access to internal email accounts, they set up email accounts that closely copy genuine addresses.

For example, someone trying to mimic info@unicornpopcorn.com might set up the account info@uncornpopcarn.com.
However, in BEC scams, the email is being sent from an already trusted and recognised address.
The impersonation element plays on the existing trust between colleagues and contemporaries, making BEC scams altogether more believable.
How common is business email compromise?
Data from the FBI indicates that BEC scams have been detected in 177 of the world’s countries.
In the UK, meanwhile, Barclays Bank suggests that as much as 55% of the money businesses lose to scammers is lost through invoice scams.
What’s the cost of an email business compromise?
In May 2022, the FBI revealed that losses from business email compromise scams have surpassed $43 billion globally.
The average small to medium UK business loses £2,100 in an invoice scam.

However, the cost of BEC attacks goes beyond the financial. These sorts of attacks can also be costly to a company’s reputation.
If a business’s customers learn that a company has been a victim of cybercrime, it could keep them from doing business with the company in the future.
The same applies to suppliers. If employee accounts have been hacked and the criminal has sent fake emails soliciting money from their suppliers, relationships with those suppliers could be damaged.
Then there’s the monetary cost of recovering from a BEC attack, including the cost of:
- The investigation following the attack
- Implementation of new security measures
- Restoration of any data lost during the attack
Related: How to protect your website from attacks
An example of business email compromise
In summer 2021, criminals hacked the email accounts of construction vendors in the US town of Peterborough.
With access to the accounts, they emailed various members of the town’s finance department asking for a number of bank transfers to be redirected to different accounts.
The scam cost the town a huge $2.3 million in total.
Four signs of a BEC attack

Although BEC scammers are clever, there are often a few tell tale signs that the message you’re reading is a spoofed email. Here are four of the most common.
- Urgency: As with many cyber security scams, BEC attackers usually invoke a sense of urgency.
This urgency encourages recipients to act hastily and without consideration.
The following can be a red flag:
- Invoices marked as overdue
- The inclusion of short deadlines in emails, for example ‘this payment must be made in 24 hours’
- Use of words and phrases like ‘immediately and ‘act now’’
- Typos: Cyber criminals may be tech wizards, but they’re not always the best at spelling and grammar.
If you receive a professional email that’s filled with typos when usually there are none, this is a major red flag. Contact the sender via a separate means and ask if the email is from them.
- Unexpected/unsolicited demands: If an email comes out of the blue or comes as a surprise to you, then there’s a chance it is part of a BEC scam.
Treat anything unexpected with caution.
- Poor quality logos: If a logo or other piece of branding in an email looks poor quality, it could be a sign that the email is a business email compromise scam.
Look out for distortions, fuzzy edges and blurriness in graphics.
How can I protect my business against a BEC scam?
There are multiple ways to improve your email security and avoid data theft — many focus on the people who are most likely to receive these emails.
Add multi-factor authentication to the email login process
Multi-factor authentication (MFA) is a login method that requires you to prove you are who you say you are in more than one way before it allows you to access your account.
It adds an extra layer of protection to the traditional authentication, which requires only a username and password.
MFA can block over 99.9% of account compromise attacks, says Microsoft.
In addition to a username and password, multi-factor authentication asks for:
- Something the user has, such as a USB or security token that acts like a sort of electronic key. Or an electronic device like a mobile phone, that’s already been shown to belong to the user, that can be sent a one-time passcode.
- Something the user knows, like a PIN or answer to a pre-defined security question such as ‘What was the name of your first pet?’
- Biometric information, such as a fingerprint, voice or iris scan.
How two factor authentication works
Step one: enter your username and password
Step two: receive a text message to your pre-registered mobile phone with a one-time passcode. Enter that code into the email account when prompted.
Insist on strong password practices
Weak passwords make it easy for cybercriminals to hack into email accounts.
If you or anyone in your company are using passwords like 12345678, qwerty or changemeplease then you’re practically rolling out the red carpet for hackers.
You should also try to avoid using anything personal in your passwords, such as a pet name or the name of your favourite football team. Cybercriminals can pick these sorts of details up from your social media profiles and have a guess at your passwords.
Strong passwords are:
- Long — at least 12 characters
- Contain a mix of upper and lowercase letters, in places you might not expect to find upper and lowercase letters — for example, miSsIssiPpiriVer
- Include a mix of numbers and symbols as well as letters, for example m1ss1ss@ppiriv#r
- Have nothing to do with your public personality

Pro tip: If you’re struggling to remember randomised passwords, try using a passphrase.
For example:
My favourite dessert is apple pie with cream and my second favourite is lemon syllabub.
To create a password from this passphrase, you take the first letter of each word and use it as your password.
So, the above passphrase translates as Mfdiapwc&m2fils.
Of course, there’s also password managers (one free), which not only suggest strong passwords but keep track of all your passwords and inserts them for you.
Make time for team training
If your team doesn’t know that BEC scams exist, then they are more likely to fall victim to one.
Don’t put off cybersecurity training.
Schedule in regular sessions when you can teach your team:
- How to spot scams
- What to do if they suspect an email may be a BEC scam
This doesn’t have to be a costly process. The UK’s National Cyber Security Centre is full of free educational resources, including the downloadable infographic below.
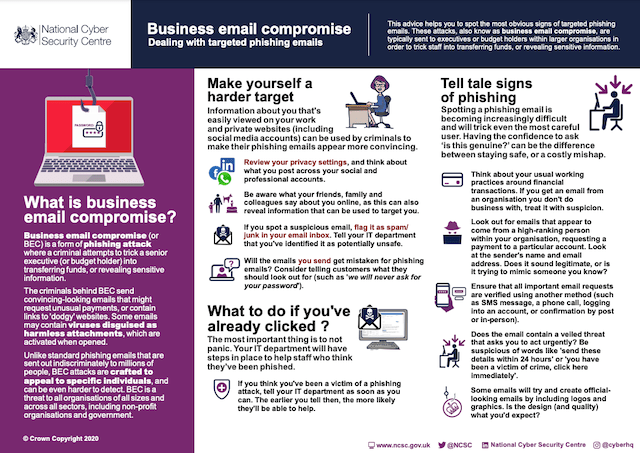
Set up a simple and easy way of reporting anything suspicious
If your business is targeted by BEC hackers, time is of the essence.
Be sure that your team knows how to report a suspicious email and who to report it to. For those who aren’t sure who to reach out to, an IT department would be a good first port of call.
What to do if you think you’re already a victim
Firstly, try not to panic.
Secondly, communicate, communicate, communicate.
Time is of the essence.
Your team members might worry that they’ll get in trouble for falling victim to a BEC scam and delay alerting anyone about it, but hackers will capitalise on this reluctance.
If your team have gone through the relevant security training, they should feel more confident in speaking. They should also know exactly who to reach out to if they suspect a BEC scam.
Finally, in the event of a BEC scam it’s important to have everyone change their log in details as quickly as possible to prevent further damage.
With a little training you can greatly reduce the chances that one of your team will misstep. Remember, knowledge is power.
Editor’s note: Working for yourself? GoDaddy can help set you up with its free logo maker, free website builder and productivity tools like Microsoft 365, including the world-famous suite of products (Excel, PowerPoint, etc).